Introduction to the Intel Management Engine OS (Part 1)
The Intel Management Engine is a secondary processor present in all modern Intel systems. This series will cover version 11.0 of the Management Engine, which is present on 6th and 7th generation Intel systems. Later versions are derived from this version.
The ME is often portrayed as a backdoor that we users have no control or insight over, and there are a number of misunderstandings perpetuated by opponents of the technology.
It is widely believed that the ME serves no legitimate purpose; this is not true. The ME originated as a seperate component used for management of enterprise systems. As systems became more integrated, it was incorporated into the PCH (southbridge), rather than the CPU. Later, Intel must have decided that it needed more sophisticated logic for initializing the clock controllers, because they moved this functionality into the ME.
Since then, the ME can no longer be disabled by removing its firmware, as it is a critical part of system bringup and thus the system will not boot without it.
So what exactly is this ME? It consists of a CPU with associated ROM, RAM and peripherals located in the PCH. It runs its own operating system, with a number of applications and drivers providing services to the host firmware and user.

For a long time, the only real resource available for researching the ME was the firmware stored in the SPI flash on the motherboard. This was especially difficult before ME version 11.0, as the earlier implementations used variants of the ARC architecture, which were not well-supported in popular reverse engineering toolchains. Despite this, some research was done and yielded a basic understanding of those versions (Skochinsky, 2014).
Research really took off in 2015 when Intel released their Sunrise Point chipset, the first to use ME 11.0. ME 11 and onwards are based on a derivative of the Intel 486 processor, which makes analysis of the code much easier.
The ME 11.0 images consist of various layers stored in the ME region of the SPI ROM (Goryachy, Ermolov, & Sklyarov, 2017). I will describe these layers in more detail later on in this series. There are easy-to-use tools available for parsing and extracting these images, such as unME11 by Dmitry Sklyarov.
The files contained in the firmware images can be divided into rougly two categories: Metadata and module files. The metadata files are parsed by the tools into human readable text files, and the module files are flat binaries containing the module code.
The ME runs a microkernel operating system which (since (Goryachy, Ermolov, & Sklyarov, 2017)) is commonly believed to be Minix. In fact, Intel use a custom microkernel (replacing the ThreadX system used before ME 11.0), which takes the POSIX VFS, system call interface and parts of the userland from Minix 3.
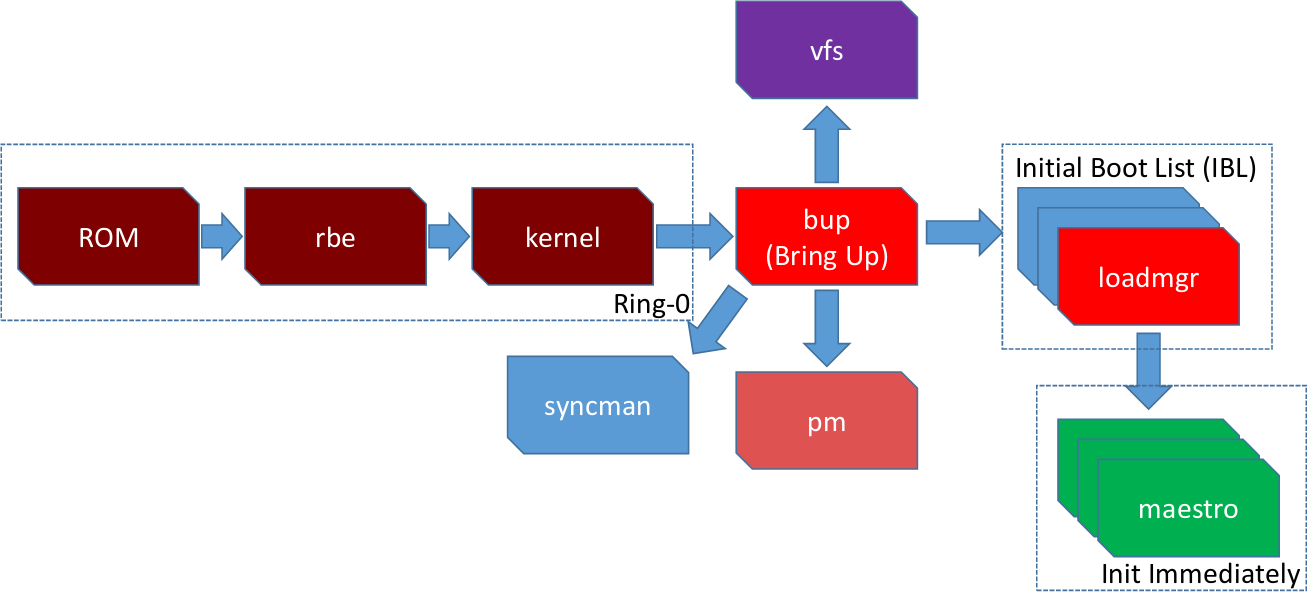 The boot flow for the ME, Image: (Goryachy, Ermolov, & Sklyarov, 2017).
The boot flow for the ME, Image: (Goryachy, Ermolov, & Sklyarov, 2017).
Microkernels have an inherent bootstrap problem, where functionality needed to load and start server processes is implemented by those same processes. The ME operation solves this by having a bringup (bup) server, which contains a barebones implementation of all services and drivers it would otherwise depend on. This module needs access to almost all core peripherals and system calls, and is thus a very interesting target when attacking the ME (Goryachy & Ermolov, 2017).
In the next article I will look into loading and analyzing a ME module
References
- Hasarfaty, S., & Moyal, Y. (2019). Behind the Scenes of Intel Security and Manageability Engine. BlackHat. Retrieved from https://i.blackhat.com/USA-19/Wednesday/us-19-Hasarfaty-Behind-The-Scenes-Of-Intel-Security-And-Manageability-Engine.pdf
- Skochinsky, I. (2014). Intel ME secrets. CODE BLUE. Retrieved from https://www.slideshare.net/codeblue_jp/igor-skochinsky-enpub
- Goryachy, M., Ermolov, M., & Sklyarov, D. (2017). Intel ME: The Way of the Static Analysis. Troopers. Retrieved from https://www.troopers.de/downloads/troopers17/TR17_ME11_Static.pdf
- Goryachy, M., Ermolov, M., & Sklyarov, D. (2017). Intel ME: Детали устройства файловой системы в Flash-памяти. RUCTF. Retrieved from https://live.ructf.org/intel_me.pdf
- Goryachy, M., & Ermolov, M. (2017). How to Hack a Turned-Off Computer, or Running Unsigned Code inIntel Management Engine. Black Hat Europe. Retrieved from https://www.blackhat.com/docs/eu-17/materials/eu-17-Goryachy-How-To-Hack-A-Turned-Off-Computer-Or-Running-Unsigned-Code-In-Intel-Management-Engine.pdf